“Copilots” for cybersecurity are one of the hottest new developments in generative AI if the ideas that keep arriving in my inbox are any guide. Microsoft possesses one. Google, as well. Vicarius, a vulnerability remediation platform, has introduced vuln_GPT, an AI tool that generates text and assists in writing scripts for system breach detection and remediation.
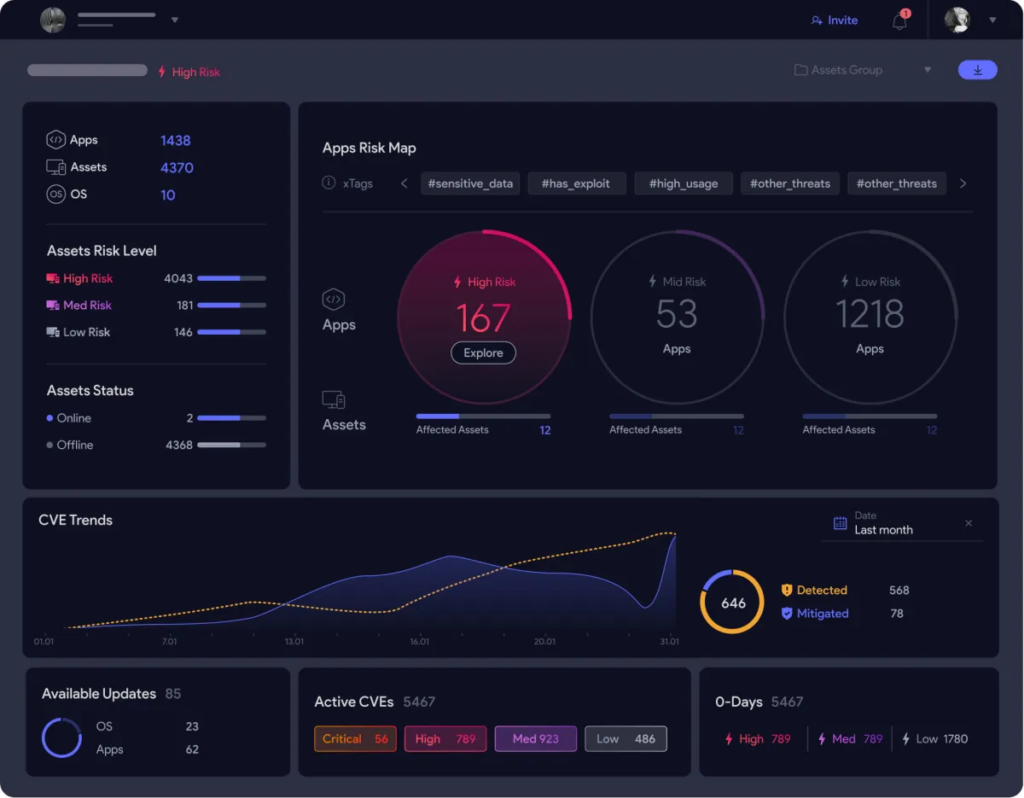
(Image Source: Techcrunch.com)
Vicarius trend-following and (I’d venture to guess) the startup’s five-fold growth year-over-year attracted investors. Michael Assraf, co-founder and CEO of Vicarius, informs me that the company’s clientele has recently surpassed 400 brands, such as Equinix, PepsiCo, and Hewlett Packard Enterprise.
Vicarius said today that it has secured a $30 million Series B investment headed by Bright Pixel Capital, with AllegisCyber Capital, AlleyCorp, and Strait Capital participation. The business is still determining what brought Vicarius to the attention of its backers. With this round, Vicarius has received approximately $56.7 million, quadrupling its prior valuation, which Assraf sadly declined to reveal. Most of the funds, according to Assraf, will go toward expanding the company’s 43-person team and furthering its product roadmap.
“A lot of the workload associated with discovery, prioritization, and remediation plagues security and IT teams are automated by Viarius,” Assraf stated. Vicarius, a pioneer in product-led growth, transforms the cybersecurity solution buyer’s mindset by enabling clients to test and discover value transparently before purchasing.
Assraf, Yossi Ze’evi, and Roi Cohen started Vicarius a few years ago after observing—at least according to Assraf—that hackers were utilizing the same “building” blocks to launch cyberattacks.
According to Assraf, “those building blocks are operating system-compiled libraries and third-party APIs supplied by software.” “Building an intelligent permission manager for system-level APIs was the main idea [with Vicarius].”
These days, Vicarius checks apps for security holes and notifies users. Vicarius employs what Assraf calls “in-memory protection” when a patch isn’t available, thus securing the program without requiring a software update (though I’m a little skeptical about that).
In addition, Vicarius provides access to a community of security vulnerability researchers where researchers can exchange repair and detection scripts and earn virtual currency for doing so. Vicarius also uses this community dataset to train its vuln_GPT. Speaking of Vuln_GPT, Assraf claims that all AI-generated scripts are “validated” before being distributed to Vicarius’ clients. Thus, it is not entirely unsupervised. (Clients may provide input on a module’s scripts.)
“We want to be clear that Vicarius wants to take the lead in AI-based vulnerability remediation at every level, from proactive remediation to prioritization and detection,” Assraf stated.
Indeed, Vicarius has big plans: to combine its platform with Jira and ServiceNow ticketing systems, offer training courses, and let security researchers in its community spend their money on products. In addition, the startup wants to expand into markets where it already operates, such as North America and Europe, as well as new ones, particularly Asia Pacific.
Assraf stated, “Enterprises have been grappling for years with implementing vulnerability management procedures that demand an excessive number of tools, generate an excessive number of alerts, and create an excessive amount of work for overworked security teams.” Businesses were exposed to cyber risk due to the vulnerability remediation cycle management’s lag despite most security processes having advanced one or two generations. Customers seek a single platform that streamlines, customizes, and expands the vulnerability mitigation process.
(Information Source: Techcrunch.com)
Hi, I am Subhranil Ghosh. I enjoy expressing my feelings and thoughts through writing, particularly on trending topics and startup-related articles. My passion for these subjects allows me to connect with others and share valuable insights.
