For the last few months, a new spyware named Erbium has been wreaking havoc on the internet. The virus, which is now disseminated with cracks and cheats for major video games, takes credit card information and passwords and breaches cryptocurrency wallets.
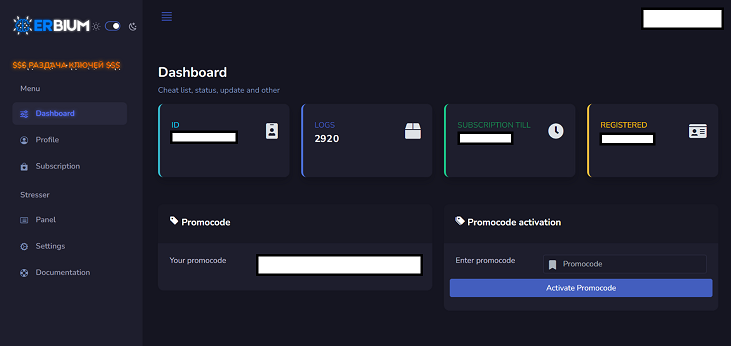
Details regarding the virus were originally highlighted by cybersecurity experts at Cluster25, who disclosed in a blog post that during the months of July when it was first gaining popularity, one could purchase a subscription to the Erbium malware for as little as $9 per week. However, the statement notes that it now costs between $100 per month and $1,000 for a year’s licence.
The stealer malware was also offered on Russian-speaking hacker forums, according to Cyfirma’s cybersecurity experts. According to the research firm’s blog post, Ebrium is being provided as a Malware-as-a-Service (MaaS), which implies that anyone with enough money may get their hands on it and even comes with ‘customer support.’
According to Cluster25 researchers, the virus has already moved to nations such as the United States, France, Spain, Italy, Vietnam, Malaysia, Colombia, and even India. Erbium is now incorporated with game cracks, but it may soon spread through other distribution mechanisms.
Erbium, like other information-stealing malwares, concentrates on collecting user data from web browsers based on Chromium and Gecko, such as Google Chrome, Microsoft Edge, and Mozilla Firefox. Passwords, cookies, autofill information, and credit card information are all stolen by the spyware. Erbium, in addition to the previously listed details, attempts to steal data from bitcoin wallets deployed as browser extensions.
According to Cyfirma, the virus comprises obfuscated material in order to prevent detection by firewalls and other security systems.
Erbium, like other information-stealing malwares, concentrates on collecting user data from web browsers based on Chromium and Gecko, such as Google Chrome, Microsoft Edge, and Mozilla Firefox. Passwords, cookies, autofill information, and credit card information are all stolen by the spyware. Erbium, in addition to the previously listed details, attempts to steal data from bitcoin wallets deployed as browser extensions.
In order to evade detection by firewalls and other security software, Research Cyfirma further notes that the virus has obfuscated components.
Some cold desktop wallets are also impacted, including Exodus, Ethereum, Litecoin-Core, Monero-Core, and Bytecoin. Erbium is also capable to stealing two-factor authentication codes from programmes such as Trezor Password Manager, Authenticator 2FA, and Authy 2FA. Furthermore, it is capable of stealing screenshots from all displays, Telegram authentication files, and even Steam and Discord credentials.
Once the virus has finished taking all data, it is sent via a built-in API interface, where operators may see in Erbium’s Dashboard what information was taken from whatever system.
Users should avoid downloading game crack files or cracked software and instead install a decent anti-virus solution and keep their systems up to date with the latest security updates.











